
Part 3: Risk Impact and Likelihood Assessment
Introduction
![[BCM] [MOM] [E3] [RAR] [T3] Risk Impact and Likelihood Assessmen](https://no-cache.hubspot.com/cta/default/3893111/fd3dd074-a74d-45ec-8219-3cee4c0463c4.png)
In Part 3, we move from identifying and listing the threat scenarios (in Part 1) to analysing their impacts and likelihoods.
The objective is to quantify (or qualitatively score) the potential impact of each threat on the Ministry of Manpower across a range of impact areas, and then calculate a risk rating (impact × likelihood).
This allows us to prioritize which threats demand more urgent attention, mitigation, or contingency planning, given limited resources.
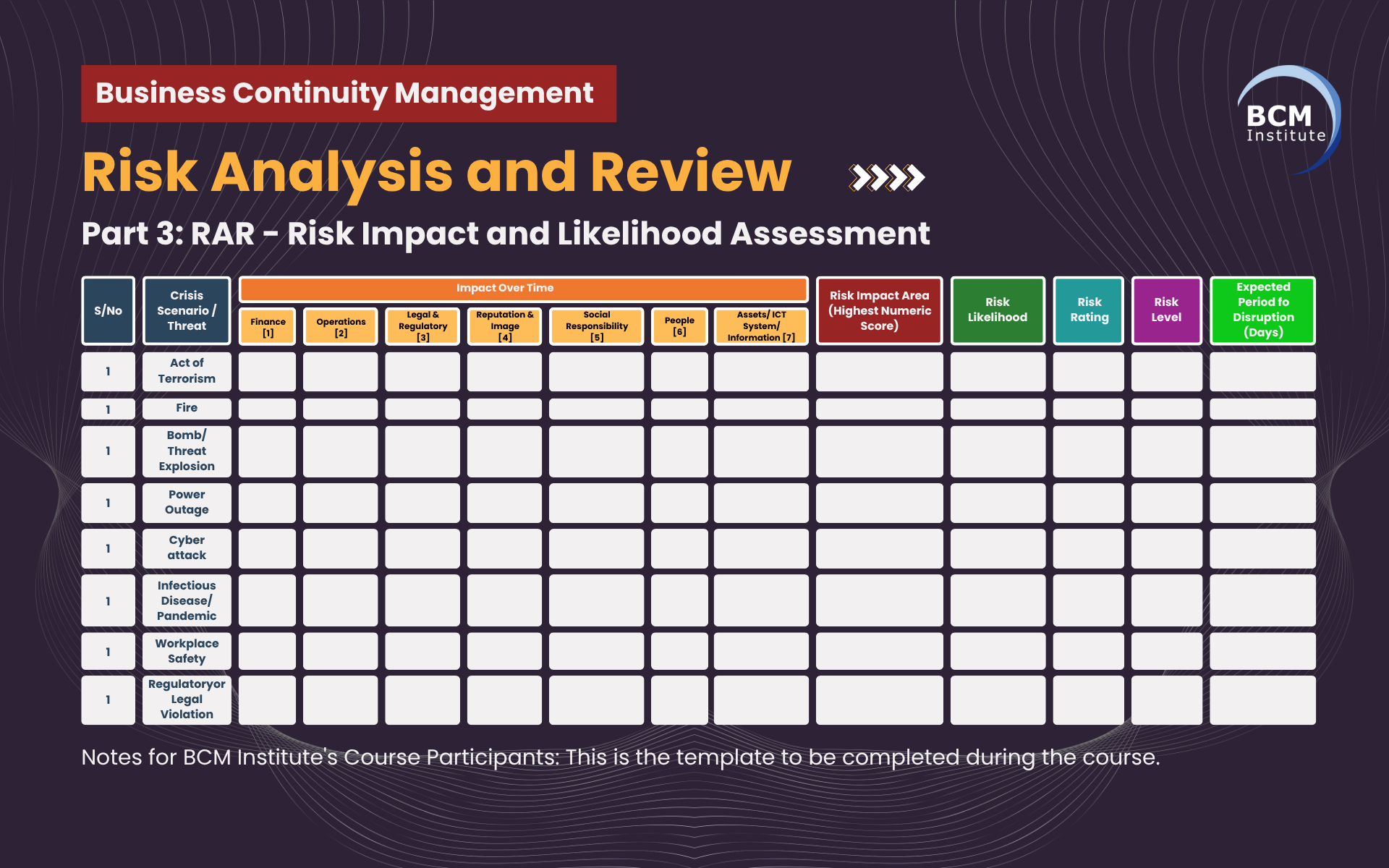
Using the BCM Planning Methodology (RAR 3-1), each threat is assessed against seven impact areas (Finance; Operations; Legal & Regulatory; Reputation & Image; Social Responsibility; People; and Assets/IT/Information)
The highest individual impact score becomes the “Risk Impact Area (Highest Numeric Score)”, which is then multiplied by the “Risk Likelihood” to derive the “Risk Rating” and thereby assign a “Risk Level” (e.g., Very Low, Low, Medium, High, Very High). Finally, we estimate how long the disruption is likely to last under that threat.
This structured tabulation guides decision-makers in selecting which threats to treat (e.g., through mitigation, transfer, acceptance, or avoidance) and informs the development of continuity plans.
Risk Impact and Likelihood Table (MOM)
Below is a template table with sample threat rows. Replace or expand with your actual threats and scoring.
|
Threat |
Impact Area – Finance |
Impact Area – Operations |
Impact Area – Legal & Regulatory |
Impact Area – Reputation & Image |
Impact Area – Social Responsibility |
Impact Area – People |
Impact Area – Assets / IT Systems / Information |
Risk Impact Area (Highest Numeric Score) |
Risk Likelihood |
Risk Rating |
Risk Level |
Expected Period of Disruption |
|
Cyberattack / data breach |
4 |
4 |
5 |
5 |
2 |
3 |
5 |
5 |
3 |
15 |
High |
2 days |
|
Major system outage (IT infrastructure) |
3 |
5 |
2 |
4 |
1 |
2 |
5 |
5 |
4 |
20 |
Very High |
1 day |
|
Regulatory non-compliance / policy violation |
2 |
3 |
5 |
4 |
1 |
2 |
1 |
5 |
2 |
10 |
Medium |
3 days |
|
Natural disaster disrupting offices |
2 |
4 |
1 |
3 |
2 |
3 |
3 |
4 |
1 |
4 |
Low |
3 days |
|
Critical staff shortage / pandemic |
1 |
4 |
2 |
3 |
2 |
5 |
1 |
5 |
3 |
15 |
High |
5 days |
|
Fraud / financial misappropriation |
5 |
2 |
4 |
4 |
1 |
1 |
1 |
5 |
2 |
10 |
Medium |
1 day |
Notes/guidance on use:
- The numeric scales (for impact and likelihood) are typically from 1 to 5, where 5 = highest.
- The “Risk Impact Area (Highest Numeric Score)” is simply the maximum of the seven impact columns for that threat.
- Risk Rating = (Highest Impact) × (Likelihood)
- The “Risk Level” is then mapped (e.g. 1-5 = Very Low, 6-10 = Low, 11-15 = Medium, 16-20 = High, etc.) depending on your risk matrix.
- The “Expected Period of Disruption” is a qualitative/estimated duration (in hours or days) that the disruption might persist if the threat materializes.
Once you have filled in all the threats from Part 1, sort or highlight the highest-rated risks so that mitigation resources can be focused on them.
Concluding Remarks (for Part 3)
By the end of this Part 3 exercise, the Ministry of Manpower will have a clear, tabulated view of which threats pose the most significant risk (i.e., combining severity of impact and probability).
The Risk Rating and Risk Level provide a structured and objective basis to rank threats, rather than relying purely on intuition.
This sets the stage for Part 4 (Risk Treatment / Mitigation / Continuity Planning): the highest-rated threats are candidates for stronger controls, redundancies, fallback plans, or even risk transfer (e.g. insurance).
Lower-risk threats might be accepted, monitored, or addressed via low-cost safeguards. In the next chapter, we will take each high-priority threat from this table and propose mitigation strategies, action plans, resource allocation, and metrics to monitor residual risk over time.
Notes
- Scoring Scale (1–5):
- 1 = Very Low
- 2 = Low
- 3 = Medium
- 4 = High
- 5 = Very High
- Likelihood Scale:
- 1 = Very Low
- 2 = Low
- 3 = Medium
- 4 = High
- 5 = Very High
- Risk Rating: Calculated as Impact x Likelihood
- Risk Level:
- 1–5: Low
- 6–14: Medium
- 15–25: High
Summing Up …
The results of the Risk Impact and Likelihood Assessment provide critical insights into the Judiciary’s exposure to various internal and external threats.
Risks such as cyberattacks, pandemics, and data breaches are assessed as having high impact and significant likelihood, highlighting the urgent need for robust controls, incident response protocols, and business continuity strategies in these areas.
This assessment also reveals that while some threats have a lower probability of occurrence (e.g., natural disasters or terrorist threats), their potential impact remains considerable and cannot be ignored.
Therefore, a balanced risk treatment approach—addressing both high-probability and high-impact scenarios—is essential.
In conclusion, this chapter equips stakeholders with a prioritised risk profile that supports informed decision-making and resource allocation.
It ensures that the Judiciary of Singapore and the State Courts can continue delivering justice effectively and efficiently, even in the face of adversity.
More Information About Business Continuity Management Courses
To learn more about the course and schedule, click the buttons below for the BCM-300 Business Continuity Management Implementer [BCM-3] and the BCM-5000 Business Continuity Management Expert Implementer [BCM-5].


![[BCM] [MOM] [E3] [BIA] MBCO Corporate MBCO](https://no-cache.hubspot.com/cta/default/3893111/91c07ac1-2f4d-4acf-a002-df50ac7e8f19.png)
![[BCM] [MOM] [E3] [BIA] [P&S] Key Product and Services](https://no-cache.hubspot.com/cta/default/3893111/904a4659-6e74-4f50-a27d-b0543463d80a.png)
![[BCM] [MOM] [E3] [RAR] [T1] List of Threats](https://no-cache.hubspot.com/cta/default/3893111/41c8981e-45dd-416c-90e0-55c3a22753da.png)
![[BCM] [MOM] [E3] [RAR] [T2] Treatment and Control](https://no-cache.hubspot.com/cta/default/3893111/02909b01-2511-4249-864b-967afcc727bc.png)
![[BCM] [MOM] [E3] [BCS] [T1] Mitigation Strategies and Justification](https://no-cache.hubspot.com/cta/default/3893111/06674b8b-3cf9-4855-a89a-ecd2baa9a395.png)
![[BCM] [MOM] [E1] [C10] Identifying Critical Business Functions](https://no-cache.hubspot.com/cta/default/3893111/f19dbb07-448c-4021-9605-82ad98643d7f.png)
![[BCM] [MOM] [E3] [BIA] [DP] [CBF] [1] Labour Market Regulation and Enforcement](https://no-cache.hubspot.com/cta/default/3893111/ff0a9479-fa3e-41a8-ba7b-9d151a715d05.png)
![[BCM] [MOM] [E3] [BIA] [T1] [CBF] [1] Labour Market Regulation and Enforcement](https://no-cache.hubspot.com/cta/default/3893111/6eaa5c4f-0bd6-4343-85a8-d94449364aa5.png)
![[BCM] [MOM] [E3] [BIA] [T2] [CBF] [1] Labour Market Regulation and Enforcement](https://no-cache.hubspot.com/cta/default/3893111/bcb5337e-1bdd-47dc-b0af-399dfc78021a.png)
![[BCM] [MOM] [E3] [BIA] [T3] [CBF] [1] Labour Market Regulation and Enforcement](https://no-cache.hubspot.com/cta/default/3893111/bbc0c267-3d28-497d-9504-5d1853058e7b.png)
![[BCM] [MOM] [E3] [BCS] [T2] [CBF] [1] Recovery Strategies](https://no-cache.hubspot.com/cta/default/3893111/c295a198-de84-41b2-be64-0a5d39bf87fe.png)
![[BCM] [MOM] [E3] [BCS] [T3] [CBF] [1] Minimum Resources Required during a Disaster](https://no-cache.hubspot.com/cta/default/3893111/68673062-6e5b-4e51-9226-4da013aaaa0e.png)
![[BCM] [MOM] [E3] [PD] [CBF] [1] Labour Market Regulation and Enforcement](https://no-cache.hubspot.com/cta/default/3893111/2ef54310-5f33-42cd-874b-187f278267ee.png)


![Register [BL-B-3]*](https://no-cache.hubspot.com/cta/default/3893111/ac6cf073-4cdd-4541-91ed-889f731d5076.png)



![FAQ [BL-B-3]](https://no-cache.hubspot.com/cta/default/3893111/b3824ba1-7aa1-4eb6-bef8-94f57121c5ae.png)
![Email to Sales Team [BCM Institute]](https://no-cache.hubspot.com/cta/default/3893111/3c53daeb-2836-4843-b0e0-645baee2ab9e.png)





