Introduction
In the second phase of the Business Continuity Management (BCM) Planning Methodology for SHINE Children and Youth Services, the focus shifts to Risk Analysis and Review (RAR).
This phase involves identifying threats and assessing their potential impact on the organisation.
Once threats are identified, risk treatment and controls must be implemented to manage these risks effectively.
In this chapter, we will examine the threats SHINE faces, how they are currently addressed, and what additional controls could further mitigate these risks.
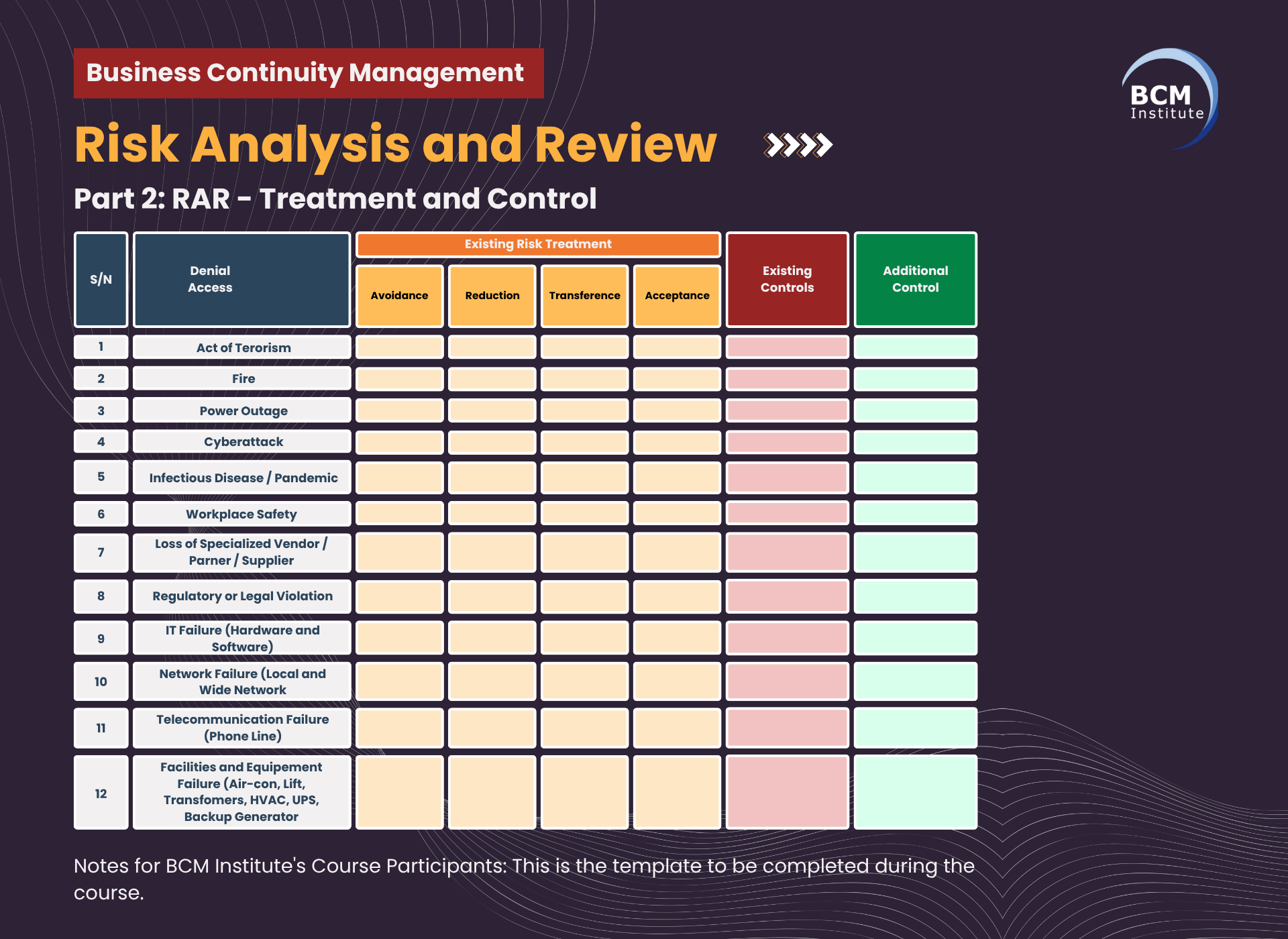
The treatment of identified risks can be categorised into four broad strategies: Risk Avoidance, Risk Reduction, Risk Transference, and Risk Acceptance.
Each threat must be analysed to determine which treatment is most suitable for mitigating its potential impact on SHINE’s operations. This chapter will outline the current treatment strategies, existing controls, and planned additional controls for each identified threat.
Table R2: Threats and Risk Treatment
|
Threat |
Existing Risk Treatment - Risk Avoidance |
Existing Risk Treatment - Risk Reduction |
Existing Risk Treatment - Risk Transference |
Existing Risk Treatment - Risk Acceptance |
Existing Controls |
Additional (Planned) Controls |
|
Denial of Access – Natural Disaster |
Relocation of operations to unaffected areas |
Emergency evacuation plans, backup sites |
Insurance coverage for damages and disruptions |
Minimal staff presence during disasters |
Emergency response protocols, disaster recovery sites |
Investment in off-site cloud storage, staff relocation exercises |
|
Denial of Access – Man-made Disaster |
Diversification of key suppliers and partners |
Increased security measures, site fencing |
Legal contracts with third-party providers to share risks |
Accept limited access to certain facilities in case of an attack |
Security guards, video surveillance, and building reinforcement |
Regular security drills, review of third-party risk management |
|
Unavailability of People |
Cross-training employees for key roles |
Remote working arrangements, flexible hours |
Outsourcing roles or hiring temporary staff |
Accept some level of absenteeism during crises |
Staff contingency plans, part-time and freelance staff |
Establish partnerships with staffing agencies, further remote work capabilities |
|
Disruption to the Supply Chain |
Diversified supply chain sources |
Stockpiling essential materials, local suppliers |
Contracts with suppliers to ensure business continuity |
Accept minor delays in non-critical supplies |
Supplier agreements, vendor relationships, and alternate suppliers |
Long-term supplier agreements, additional local suppliers |
|
Equipment and IT-Related Disruption |
Cloud migration, automation for critical systems |
Regular system maintenance, backup power supplies |
IT support and service level agreements (SLAs) with third parties |
Accept some system downtime for non-essential systems |
Backup servers, UPS (uninterruptible power supply), firewalls |
Implement AI-based monitoring, disaster recovery systems |
In conclusion, the treatment and control of risks at SHINE Children and Youth Services are ongoing processes that require proactive management and regular updates.
The threats SHINE faces, including natural and man-made disasters, supply chain disruptions, and IT-related issues, pose significant risks to the organisation’s ability to provide uninterrupted services.
By employing a comprehensive risk treatment strategy that incorporates risk avoidance, reduction, transference, and acceptance, SHINE ensures that it can continue its mission effectively.
The current controls in place, such as backup systems, security measures, and supplier contracts, provide a solid foundation for managing threats.
However, as the environment evolves, it is crucial to continue improving these controls. The additional planned controls, such as further cloud migrations, enhanced security measures, and new supplier agreements, will bolster SHINE’s resilience and ability to maintain its critical services even in the face of crises.
Ultimately, this chapter has outlined a dynamic approach to risk management, ensuring SHINE’s operational continuity while fostering a culture of preparedness and resilience within the organisation.
More Information About Business Continuity Management Courses
To learn more about the course and schedule, click the buttons below for the BCM-300 Business Continuity Management Implementer [BCM-3] and the BCM-5000 Business Continuity Management Expert Implementer [BCM-5].





![[BCM] [SHINE] [E3] [RAR] [T2] Treatment and Control](https://no-cache.hubspot.com/cta/default/3893111/08e6836a-0f79-4ea5-8059-07eaf1cf927c.png)

![Banner [Table] [BCM] [E3] [RAR] [Summing Up] [T2] Treatment and Control of Identified Threats](https://no-cache.hubspot.com/cta/default/3893111/6755d2e8-5050-4a5e-be0a-a1568a65e0ed.png)
![[BCM] [SHINE] [E3] [BIA] MBCO Corporate MBCO](https://no-cache.hubspot.com/cta/default/3893111/8a4c1bad-b882-4431-9db9-564f8d734724.png)
![[BCM] [SHINE] [E3] [BIA] [PS] Key Product and Services](https://no-cache.hubspot.com/cta/default/3893111/5e23190b-1be3-4bd9-b9f4-ea90013c9628.png)
![[BCM] [SHINE] [E3] [RAR] [T1] List of Threats](https://no-cache.hubspot.com/cta/default/3893111/999fd75b-6269-41c1-b833-e44ec6e1be72.png)
![[BCM] [SHINE] [E3] [RAR] [T3] Risk Impact and Likelihood Assessment](https://no-cache.hubspot.com/cta/default/3893111/dfeec650-fd4f-4916-b353-f6860d9e4393.png)
![[BCM] [SHINE] [E3] [BCS] [T1] Mitigation Strategies and Justification](https://no-cache.hubspot.com/cta/default/3893111/03fd32a8-7ffe-4c0b-9eef-a32cb67f2e61.png)
![[BCM] [SHINE] [E1] [C10] Identifying Critical Business Functions](https://no-cache.hubspot.com/cta/default/3893111/6fba5a23-5e02-4368-aa88-65a252d4edd7.png)


![Register [BL-B-3]*](https://no-cache.hubspot.com/cta/default/3893111/ac6cf073-4cdd-4541-91ed-889f731d5076.png)



![FAQ [BL-B-3]](https://no-cache.hubspot.com/cta/default/3893111/b3824ba1-7aa1-4eb6-bef8-94f57121c5ae.png)
![Email to Sales Team [BCM Institute]](https://no-cache.hubspot.com/cta/default/3893111/3c53daeb-2836-4843-b0e0-645baee2ab9e.png)





