Chapter 3
Business Continuity Management Planning Methodology for the Employment and Employability Institute
![[BCM] [e2i] [E2] [C3] Risk Analysis and Review](https://no-cache.hubspot.com/cta/default/3893111/ddf31279-f0b1-43fd-9701-af04885fb3b2.png) The Risk Analysis and Review phase is a critical component of the Business Continuity Management (BCM) planning methodology.
The Risk Analysis and Review phase is a critical component of the Business Continuity Management (BCM) planning methodology.
It enables organisations such as the Employment and Employability Institute (e2i) to understand, assess, and address threats that may impede their ability to deliver essential services.
This proactive step ensures that appropriate controls are in place and that the risk landscape is continuously monitored and updated in line with e2i’s strategic objectives and operational environment.
1. Identifying Risks
The first step involves systematically identifying potential threats to e2i’s operations.
Given the organisation’s mandate to support the employment and employability needs of Singapore’s workforce, various internal and external risk sources must be considered.
Examples of Potential Risks at e2i
- IT System Downtime: e2i’s online platforms and job matching systems are central to its service delivery. A cyber-attack, data breach, or system failure could disrupt services such as career coaching, job applications, and skills upgrading support.
- Pandemic or Public Health Emergency: A resurgence of an infectious disease (e.g., COVID-19) could limit physical engagement at e2i career centres and postpone in-person training or job fairs.
- Vendor or Partner Dependency: e2i works closely with training providers, employers, and government agencies. Disruption in any of these partnerships due to financial failure or non-compliance could affect programme delivery.
- Regulatory Changes: Sudden changes in national manpower policies or funding guidelines may require immediate operational adjustments.
- Reputation Risk: Negative publicity arising from unsuccessful programme outcomes or public grievances could reduce stakeholder trust and affect funding.
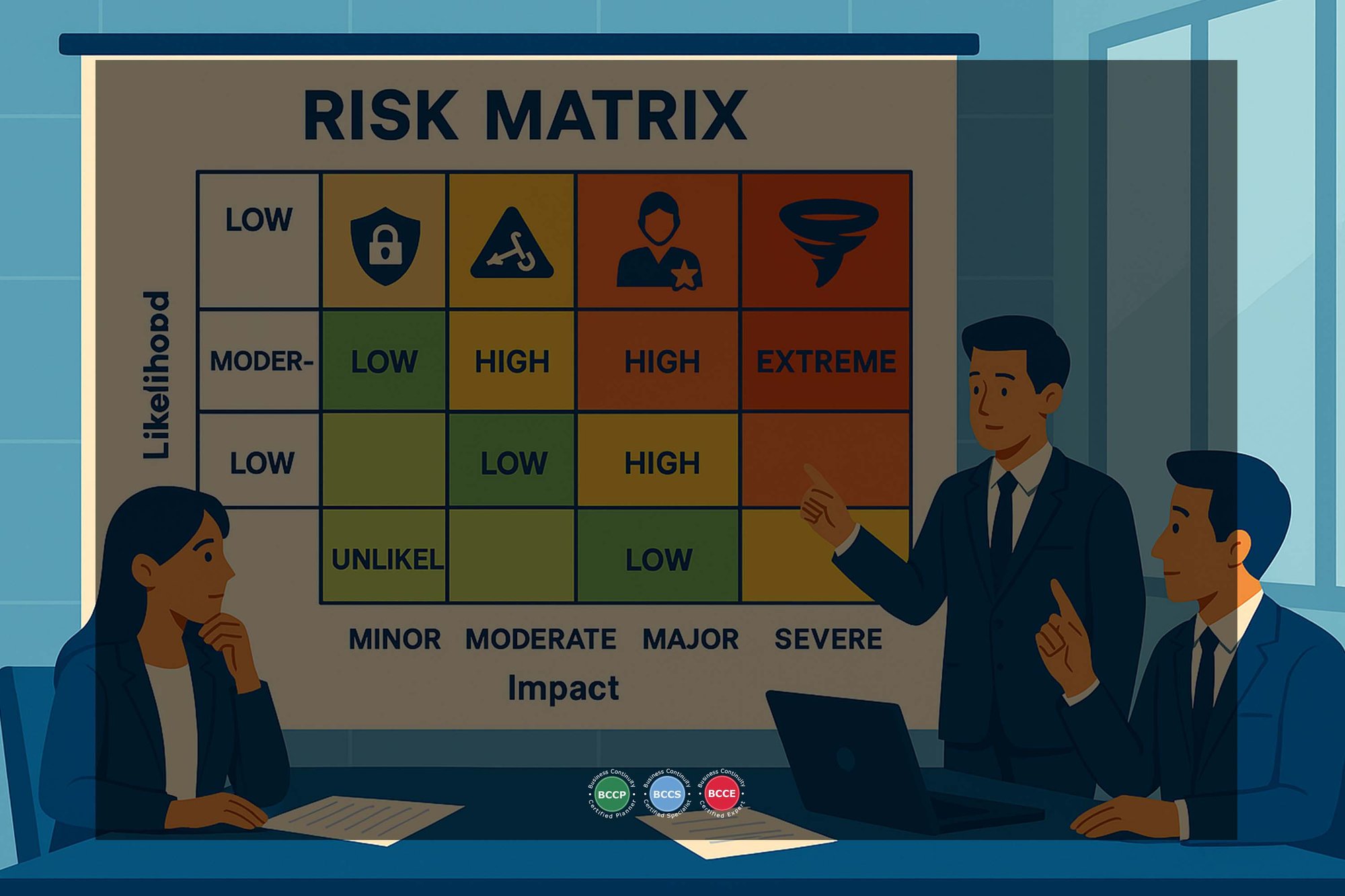
2. Assessing Risks
Once risks are identified, each is evaluated based on two criteria: likelihood (probability of occurrence) and impact (extent of potential disruption).
This allows e2i to prioritise threats and allocate mitigation resources efficiently.
Sample Risk Assessment Matrix for e2i
|
Risk Event |
Likelihood |
Impact |
Risk Rating |
|
Cyber-attack on e2i portal |
Medium |
High |
High |
|
Partner non-compliance |
High |
Medium |
High |
|
Minor regulatory change |
High |
Low |
Medium |
|
Major public health outbreak |
Low |
High |
Medium |
|
Data breach of job seeker info |
Medium |
High |
High |
This analysis provides e2i with a clear understanding of where its most critical vulnerabilities lie and which areas require immediate action or continuous monitoring.
3. Mitigating Risks
With the risk profile established, e2i must develop and implement appropriate controls to either reduce the likelihood of risk events or minimise their impact.
Mitigation strategies should be practical, cost-effective, and tailored to e2i’s operational structure.
Examples of Risk Mitigation Measures at e2i
- Cybersecurity Controls: Implementing multi-factor authentication, endpoint detection and response (EDR) systems, and regular vulnerability assessments to safeguard digital assets.
- Alternative Service Channels: Strengthening digital channels (e.g., virtual career coaching, online job fairs) to ensure continuity during physical disruptions.
- Partner Due Diligence and Monitoring: Establishing clear compliance frameworks and performance KPIs for third-party providers and regularly reviewing their adherence.
- Crisis Communication Plan: Preparing communication templates and media handling protocols to protect e2i’s brand and reassure stakeholders during incidents.
- Data Recovery Plan: Developing tested backup and restoration processes for all critical information systems.
4. Continuous Review
Risk is not static. As e2i evolves to meet emerging employment trends, and as the external environment shifts (e.g., technology advancement, demographic changes, geopolitical uncertainties), the organisation must regularly review and update its risk assessments and mitigation strategies.
Continuous Review Practices:
- Annual BCM Risk Workshops: Conducting cross-departmental risk review sessions to revalidate assumptions and uncover new threats.
- Quarterly Risk Register Updates: Updating the central risk register with new risks, revised ratings, or mitigated threats.
- Post-Incident Reviews: After every incident or near-miss, conduct a review to assess the adequacy of existing controls and update procedures accordingly.
- Stakeholder Engagement: Gathering feedback from internal teams, job seekers, and partners to identify overlooked or emerging concerns.
Summing Up ...
Through structured risk analysis and review, e2i ensures that its operations remain resilient in the face of uncertainty.
By identifying and understanding key risks, assessing their potential impact, implementing robust mitigation strategies, and maintaining an active review cycle, e2i demonstrates a strong commitment to service continuity and stakeholder confidence—core principles aligned with the ISO 22301 standard for Business Continuity Management Systems.
This phase not only prepares e2i to respond effectively to disruptive events but also reinforces its role as a trusted and agile institution dedicated to supporting the employment needs of Singapore’s workforce.
Ensuring Service Continuity: BCM Implementation for Employment & Employability |
||||
| eBook 2: Implementing BCM Planning Methodology | ||||
![[BCM] [e2i] [E2] [C1] Business Continuity Management Planning Methodology](https://no-cache.hubspot.com/cta/default/3893111/2fd80133-8311-4294-b21a-c222e1c51953.png) |
![[BCM] [e2i] [E2] [C2] Project Management](https://no-cache.hubspot.com/cta/default/3893111/afa54ac1-1864-4c08-9413-4775a5d40244.png) |
![[BCM] [e2i] [E2] [C3] Risk Analysis and Review](https://no-cache.hubspot.com/cta/default/3893111/ddf31279-f0b1-43fd-9701-af04885fb3b2.png) |
![[BCM] [e2i] [E2] [C4] Business Impact Analysis](https://no-cache.hubspot.com/cta/default/3893111/6eead46c-f973-4840-b908-31c7bac24f2e.png) |
![[BCM] [e2i] [E2] [C5] Business Continuity Strategy](https://no-cache.hubspot.com/cta/default/3893111/a5378c6d-80a8-4ea6-9547-416eb9d4e96b.png) |
![[BCM] [e2i] [E2] [C6] BCM Plan Development](https://no-cache.hubspot.com/cta/default/3893111/16d930df-7279-4fca-bb75-7541f7e77cb0.png) |
![[BCM] [e2i] [E2] [C7] Testing and Exercising](https://no-cache.hubspot.com/cta/default/3893111/9bfda004-0c39-488a-9cf2-e4c84294b7b3.png) |
![[BCM] [e2i] [E2] [C8] Program Management](https://no-cache.hubspot.com/cta/default/3893111/539e5be1-a040-4bd2-b9ea-3bd81047785e.png) |
![[BCM] [e2i] [E2] [C9] Summary](https://no-cache.hubspot.com/cta/default/3893111/4f6689c5-4e37-4155-b13f-8f1ce2972273.png) |
![[BCM] [e2i] [E2] [C10] Back Cover for BCM](https://no-cache.hubspot.com/cta/default/3893111/0c16f25f-6f42-4d3a-b87b-f3efb3a54b72.png) |
More Information About Business Continuity Management Courses
To learn more about the course and schedule, click the buttons below for the BCM-300 Business Continuity Management Implementer [BCM-3] and the BCM-5000 Business Continuity Management Expert Implementer [BCM-5].





![Register [BL-B-3]*](https://no-cache.hubspot.com/cta/default/3893111/ac6cf073-4cdd-4541-91ed-889f731d5076.png)



![FAQ [BL-B-3]](https://no-cache.hubspot.com/cta/default/3893111/b3824ba1-7aa1-4eb6-bef8-94f57121c5ae.png)
![Email to Sales Team [BCM Institute]](https://no-cache.hubspot.com/cta/default/3893111/3c53daeb-2836-4843-b0e0-645baee2ab9e.png)





