Introduction
![List of Threats and Crisis Scenarios [Part 2]](https://no-cache.hubspot.com/cta/default/3893111/9db82500-8cd2-4127-8eaf-82a39b4c063b.png) As a fully licensed digital bank under Bank Negara Malaysia and the Ministry of Finance, YTL Digital Bank Berhad (Ryt Bank) operates in a rapidly evolving financial ecosystem where technological innovation intersects with increasing operational risk exposure. This chapter initiates the Risk Assessment and Review (RAR) process by identifying a comprehensive list of potential threats that could impact the bank’s critical operations, digital infrastructure, and customer service delivery.
As a fully licensed digital bank under Bank Negara Malaysia and the Ministry of Finance, YTL Digital Bank Berhad (Ryt Bank) operates in a rapidly evolving financial ecosystem where technological innovation intersects with increasing operational risk exposure. This chapter initiates the Risk Assessment and Review (RAR) process by identifying a comprehensive list of potential threats that could impact the bank’s critical operations, digital infrastructure, and customer service delivery.
Given Ryt Bank’s reliance on digital platforms, cloud infrastructure, and third-party providers, combined with its commitment to inclusive, customer-centric banking, understanding its threat landscape is paramount.
The threat categories examined include natural and man-made disasters, people-related disruptions, supply chain vulnerabilities, and technology or system failures.
This threat identification is designed to enable the Bank to proactively implement resilience strategies and establish a robust foundation for risk treatment and controls in subsequent phases of operational resilience planning.
This section is developed in alignment with the BCM Institute's Operational Resilience Planning Methodology, incorporating both external (country-level) and internal (organisation-level) considerations to ensure comprehensive threat awareness.
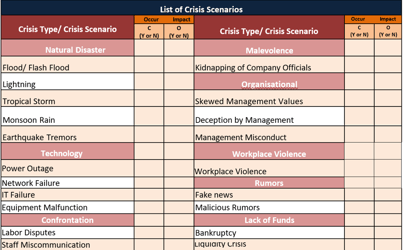
List of Threats/ Crisis Scenarios for Ryt Bank [3 to 8]
Table Below: Notes for BCM Institute's Course Participants: This is the template for completing the "Part 1: CRA – List of Threats."
Part 1: CRA – List of Threats/Crisis Scenario for Ryt Bank [3 to 8]
|
Crisis Type |
Type of Crisis Scenario |
Description of Crisis Scenario |
Country Level |
Organisation Level |
|
Confrontation |
Industrial Dispute |
Employee strike, union protest due to poor working conditions or job insecurity |
Yes |
Yes |
|
Confrontation |
Activism |
Stakeholder confrontation over ESG or digital privacy concerns |
Yes |
Yes |
|
Malevolence |
Cybercrime – Ransomware |
Criminal actors encrypt Ryt Bank systems, demanding ransom |
Yes |
Yes |
|
Malevolence |
Social Engineering |
Phishing leading to credential compromise or financial loss |
Yes |
Yes |
|
Org Misdeeds – Skewed Values |
Profit Above Ethics |
Management disregards compliance in pursuit of growth |
Yes |
Yes |
|
Org Misdeeds – Deception |
Hidden Breach |
Withholding disclosure of a data breach from regulators or the public |
Yes |
Yes |
|
Org Misdeeds – Misconduct |
Insider Trading / Bribery |
Executives caught in unethical practices or collusion |
Yes |
Yes |
|
Due to Workplace Violence |
Physical Harm |
Aggression between staff or external threats entering the premises |
Low |
Yes |
|
Due to Rumours |
Fake News |
Viral misinformation on app shutdown or bank license being revoked |
Yes |
Yes |
|
Lack of Funds |
Liquidity Crunch |
Poor financial planning resulting in capital shortfalls |
Yes (esp. in a crisis economy) |
Yes |
Legend
- Country Level: Whether the threat is likely to affect Malaysia or has precedent at a national level.
- Organisation Level: Whether the threat can directly disrupt Ryt Bank’s operations, reputation, or compliance.
Conclusion
This chapter has outlined the broad spectrum of threats that may affect Ryt Bank’s ability to maintain continuous and reliable banking operations in a digitally driven environment.
By systematically categorising and describing each threat—ranging from floods and cyberattacks to cloud outages and workforce disruptions—Ryt Bank reinforces its commitment to anticipating disruptions before they occur.
This foundational threat register serves as the basis for developing deeper risk treatment, controls, and resilience strategies, which are addressed in the following chapters.
With a clear understanding of both external risks and internal vulnerabilities, Ryt Bank is better positioned to uphold customer trust, regulatory compliance, and operational integrity, no matter the crisis scenario.
Crisis Management Blueprint for Ryt Bank |
||||||
| eBook 3: Starting Your Crisis Management Implementation | ||||||
![[CM] [RYT] [E1] [C1] Overview of Case Study for Ryt Bank](https://no-cache.hubspot.com/cta/default/3893111/68a9bbd6-2838-498a-a618-0e30b5ba4a5d.png) |
![[CM] [RYT] [E1] [C2] Understanding Your Organisation](https://no-cache.hubspot.com/cta/default/3893111/89526c07-4d15-44d3-aac3-e0be034e6ae5.png) |
![[CM] [TS] [E1] [C3] Establishing CM Goals](https://no-cache.hubspot.com/cta/default/3893111/159179c7-f1c8-412a-9133-d9e58cf3abdd.png) |
![[CM] [RYT] [E1] [C4] CM Vs BCM](https://no-cache.hubspot.com/cta/default/3893111/bbea09e8-e1c7-4d77-bf9c-f69152a9238f.png) |
![[CM] [RYT] [E1] [C5] Identifying the Types of Crisis Scenarios](https://no-cache.hubspot.com/cta/default/3893111/bd0ae39c-0686-4d0b-a7c2-4d3e05ad8fe2.png) |
![[CM] [RYT] [E1] [C5A] Technological Crisis Scenarios](https://no-cache.hubspot.com/cta/default/3893111/d2410cf1-7123-4934-9ccd-9a8341e86645.png) |
|
![[CM] [RYT] [E1] [C6] Assessing Risks and Threats](https://no-cache.hubspot.com/cta/default/3893111/9fe8d89e-6aa7-4c44-8aaa-1fb006fffbca.png) |
![[CM] [RYT] [E1] [C7] Composing the CM Team](https://no-cache.hubspot.com/cta/default/3893111/9c22ccbb-eff7-4a33-92ae-32478b8bc6d4.png) |
![[CM] [RYT] [E1] [C8] Implementing the CM Planning Methodology](https://no-cache.hubspot.com/cta/default/3893111/2d189dba-1361-4ae0-bb86-67d926848caf.png) |
![[CM] [RYT] [E1] [C9] Pre-Crisis - Risk Identification and Crisis Preparedness](https://no-cache.hubspot.com/cta/default/3893111/1ba23c14-9c14-4cbe-b82b-ebc9ff159127.png) |
![[CM] [RYT] [E1] [C10] During Crisis - Crisis Response and Decision-Making](https://no-cache.hubspot.com/cta/default/3893111/58d0552a-e73f-45bc-87d1-61beda7e4847.png) |
![[CM] [RYT] [E1] [C11] Post Crisis - Crisis Recovery](https://no-cache.hubspot.com/cta/default/3893111/78f12da7-ae09-4fe1-8bae-6794e1e732dc.png) |
![[CM] [RYT] [E1] [C12] Summary and Strategic Outlook](https://no-cache.hubspot.com/cta/default/3893111/84317665-f46a-410f-86be-abb5e3d0f684.png) |
More Information About Crisis Management Blended/ Hybrid Learning Courses
To learn more about the course and schedule, click the buttons below for the CM-300 Crisis Management Implementer [CM-3] and the CM-5000 Crisis Management Expert Implementer [CM-5].



![[CM] [E3] [Risk Assessment] List of Threats and Crisis Scenario [Part 1] (2)](https://blog.bcm-institute.org/hs-fs/hubfs/RYT%20eBook%20Blog%20Banner/RYT%20E3%20Long%20Banner/%5BCM%5D%20%5BE3%5D%20%5BRisk%20Assessment%5D%20List%20of%20Threats%20and%20Crisis%20Scenario%20%5BPart%201%5D%20(2).png?width=1920&height=220&name=%5BCM%5D%20%5BE3%5D%20%5BRisk%20Assessment%5D%20List%20of%20Threats%20and%20Crisis%20Scenario%20%5BPart%201%5D%20(2).png)





![[BL-CM] [5] Register](https://no-cache.hubspot.com/cta/default/3893111/82024308-16f4-4491-98be-818a882c6286.png)

![Email to Sales Team [BCM Institute]](https://no-cache.hubspot.com/cta/default/3893111/3c53daeb-2836-4843-b0e0-645baee2ab9e.png)





