
Part 2: RAR - Treatment and Control
 Part 2: RAR – Treatment and Control
Part 2: RAR – Treatment and Control

 This section maps each key threat category to the corresponding controls, both existing and proposed, to illustrate Bandtree’s readiness and ongoing efforts in mitigating operational and strategic risks.
This section maps each key threat category to the corresponding controls, both existing and proposed, to illustrate Bandtree’s readiness and ongoing efforts in mitigating operational and strategic risks.
By implementing and continually refining these risk management measures, Bandtree ensures alignment with best practices in business continuity management (BCM).
It demonstrates its commitment to delivering sustainable, secure, and reliable services.
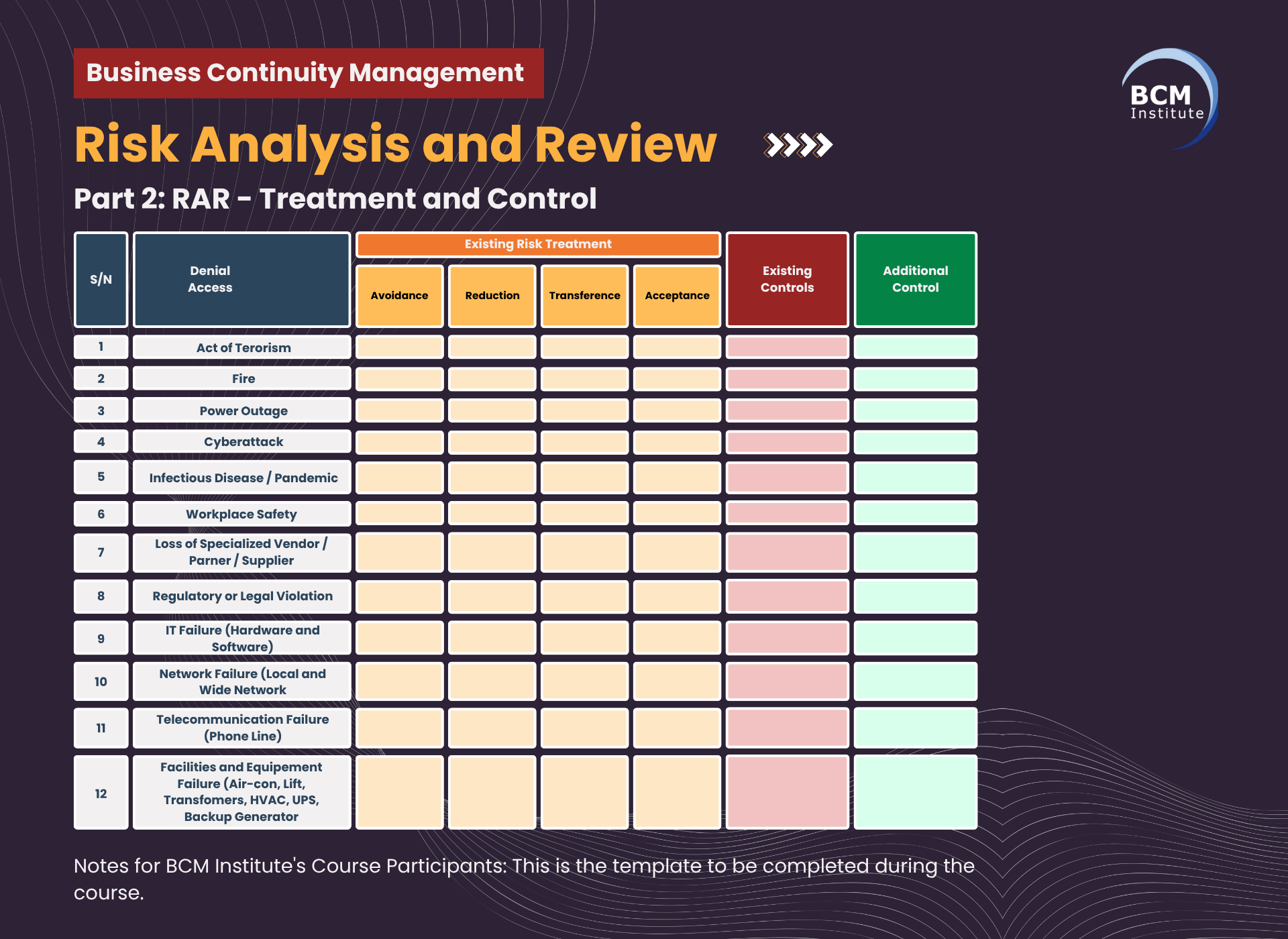
Table 2-1: [RAR] [T2] Treatment and Control for Bandtree
| Existing Risk Treatment |
||||
|
Threat |
Risk Avoidance |
Risk Reduction |
Risk Transference |
Risk Acceptance |
|
Denial of Access – Natural Disaster (e.g. flood, earthquake) |
Avoid development in flood-prone areas or geologically unstable zones. |
Elevated building design, stormwater drainage system, and emergency power backup (generators). |
Insurance coverage for natural disasters impacting assets. |
Accept limited downtime in less critical sites. |
|
Denial of Access – Man-made Disaster (e.g. fire, terrorism) |
Avoid hosting high-risk tenants or operations in politically sensitive areas. |
Fire suppression systems, fire-resistant materials, 24/7 CCTV monitoring, and physical access control. |
Property and liability insurance. |
Accept short-term disruptions in the event of isolated incidents. |
|
Unavailability of People (e.g. pandemic, strikes) |
Avoid overreliance on critical staff by cross-training personnel to ensure continuity of operations. |
Implement flexible work arrangements, health protocols, vaccination drives, and remote work infrastructure (VPN, collaboration tools). |
Outsourcing of non-core functions or temporary manpower sourcing. |
Accept a temporary drop in productivity during extreme cases. |
|
Disruption to the Supply Chain (e.g. vendors, spare parts) |
Avoid single-vendor dependencies. |
Maintain a buffer stock of critical supplies, conduct periodic vendor risk assessments, and utilise a diversified supplier base. |
Vendor contracts with performance and penalty clauses. |
Accept minor delays in low-impact services. |
|
Equipment and IT-Related Disruption (e.g. server failure) |
Avoid unsupported or legacy systems. |
Regular IT maintenance, scheduled backups, asset lifecycle management, disaster recovery planning, and power surge protectors. |
IT support service contracts with third-party providers. |
Accept tolerable downtime for non-critical systems. |
Table 2-2: [RAR] [T2] Treatment and Control for Bandtree
|
Threat |
Existing Controls |
Additional (Planned) Controls |
|
Denial of Access – Natural Disaster (e.g. flood, earthquake) |
Business Continuity Plan (BCP), structural safety audits, emergency evacuation plans. |
Installation of early warning systems, remote work readiness drills, periodic flood risk mapping, and elevated storage for critical records. |
|
Denial of Access – Man-made Disaster (e.g. fire, terrorism) |
Emergency response team (ERT), fire drills, access logs, secure ID access, and collaboration with the fire department. |
Conduct biannual fire safety audits, implement biometric access, upgrade to innovative security systems, and enhance incident communication protocols. |
|
Unavailability of People (e.g. pandemic, strikes) |
HR contingency plans, succession planning, regular staff wellness checks, and flexible leave policies. |
Invest in workforce management systems, maintain a standby pool of trained temps, and strengthen telecommuting policies. |
|
Disruption to the Supply Chain (e.g. vendors, spare parts) |
Approved Vendor List (AVL), quarterly vendor reviews, and critical supplier SLAs. |
Establish an alternative supplier framework, digitise inventory tracking, and enhance visibility into Tier 2 vendors. |
|
Equipment and IT-Related Disruption (e.g. server failure) |
Antivirus software, network monitoring, firewalls, and redundant connectivity. |
Migrate core systems to cloud infrastructure, conduct annual disaster recovery (DR) testing, enhance endpoint security, and install uninterruptible power supplies (UPS) for all workstations. |
Summing Up ...
The RAR Treatment and Control framework presented in this chapter provides a comprehensive overview of Bandtree's proactive stance in addressing potential threats to its operations.
Through a balanced combination of risk avoidance, reduction, transference, and acceptance, Bandtree strengthens its organisational resilience and safeguards its core mission in supporting Brunei’s infrastructure and real estate development.
While existing controls form a solid foundation, the inclusion of planned enhancements reflects a forward-looking strategy that embraces continuous improvement.
These efforts ensure that Bandtree remains adaptable in the face of evolving risks and regulatory expectations.
Ultimately, the effectiveness of this risk treatment approach lies in its integration across the organisation, from operational planning to strategic decision-making, ensuring that Bandtree remains not only operationally robust but also trusted as a critical national asset.
More Information About Business Continuity Management Courses
To learn more about the course and schedule, click the buttons below for the BCM-300 Business Continuity Management Implementer [BCM-3] and the BCM-5000 Business Continuity Management Expert Implementer [BCM-5].



















![Register [BL-B-3]*](https://blog.bcm-institute.org/hs-fs/hubfs/hub_generated/resized/19a8306f-6b76-45ff-8585-95111f393aeb.png?width=200&height=56&name=19a8306f-6b76-45ff-8585-95111f393aeb.png)



![FAQ [BL-B-3]](https://blog.bcm-institute.org/hs-fs/hubfs/hub_generated/resized/9b7f5669-8ad6-450b-a98f-5f5d49ebfc8e.png?width=150&height=150&name=9b7f5669-8ad6-450b-a98f-5f5d49ebfc8e.png)
![Email to Sales Team [BCM Institute]](https://blog.bcm-institute.org/hs-fs/hubfs/hub_generated/resized/83ae9ad3-affc-416e-8f51-64218d6d98f2.png?width=100&height=100&name=83ae9ad3-affc-416e-8f51-64218d6d98f2.png)





