
BIA Questionnaires
CBF-8: Procurement & Supply Chain Management
 This chapter presents a detailed analysis of how disruptions to Bandtree’s critical business functions (CBFs) affect the organisation over time.
This chapter presents a detailed analysis of how disruptions to Bandtree’s critical business functions (CBFs) affect the organisation over time.
The assessment of “impact over time” is a crucial component of the Business Impact Analysis (BIA), as it reveals the rate at which disruption severity escalates across specific business functions and sub-processes.
By measuring the impact across defined time intervals—from as short as four hours to as long as sixty days—this analysis helps Bandtree identify which functions require urgent restoration (Recovery Time Objective – RTO) and the point beyond which disruption becomes intolerable (Maximum Tolerable Period of Disruption – MTPD).
It also highlights vulnerable periods when business functions are most at risk, such as during project milestones, audit cycles, or emergency operations.
Given Bandtree’s strategic position as a government-linked entity under Darussalam Assets, with responsibilities tied to national infrastructure and property management, ensuring the timely recovery of its critical functions is essential not only for operational continuity but also for national-level service assurance.
Based on your requirements and BCM Institute’s Impact Over Time methodology, here is a comprehensive impact analysis table for CBF-8: Procurement & Supply Chain Management of Bandtree.
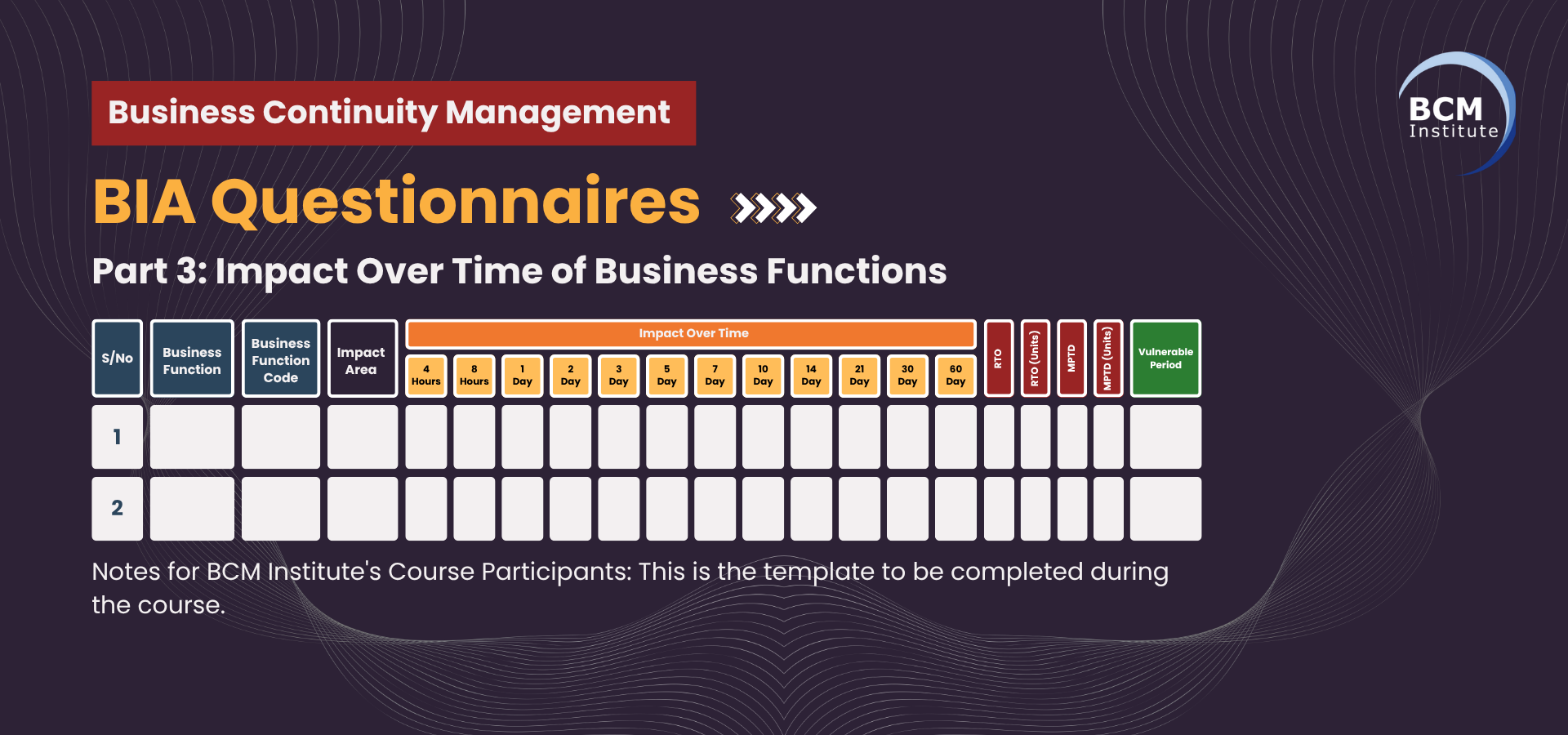
This table outlines the sub-functions (Sub-CBFs), their highest-impact area, the severity of disruption over time (rated 1–5), along with the defined Recovery Time Objective (RTO), Maximum Tolerable Period of Disruption (MTPD), and the Vulnerable Period during which the business is at critical risk.
Table 3: [BIA] [P3] Impact Over Time of Business Functions (Sub-CBF) for CBF-8: Procurement & Supply Chain Management
|
Sub-CBF |
Sub-CBF Code |
Highest-Impact Area |
4 Hr |
8 Hr |
1 Day |
2 Day |
3 Day |
5 Day |
7 Day |
10 Day |
14 Day |
21 Day |
30 Day |
60 Day |
RTO |
MTPD |
Vulnerable Period |
|
Vendor Selection & Prequalification |
8.1 |
Operational Disruption |
2 |
2 |
3 |
4 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
2 Days |
5 Days |
Start of major sourcing cycle |
|
Contract Management |
8.2 |
Legal / Compliance |
1 |
2 |
3 |
3 |
4 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
2 Days |
7 Days |
Renewal / expiration periods |
|
Purchase Requisition & Approval |
8.3 |
Operational Delay |
2 |
3 |
4 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
1 Day |
5 Days |
End-of-month ordering cycle |
|
Supplier Relationship Management |
8.4 |
Operational Risk |
2 |
2 |
3 |
3 |
4 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
3 Days |
10 Days |
During active service windows |
|
Inventory & Logistics Coordination |
8.5 |
Service Delivery |
3 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
1 Day |
3 Days |
Maintenance / project periods |
|
Compliance & Procurement Governance |
8.6 |
Regulatory Compliance |
1 |
1 |
2 |
2 |
3 |
4 |
4 |
5 |
5 |
5 |
5 |
5 |
5 Days |
14 Days |
Audit or regulatory review |
|
Risk Management in Supply Chain |
8.7 |
Strategic / Operational Risk |
1 |
2 |
3 |
3 |
4 |
4 |
4 |
5 |
5 |
5 |
5 |
5 |
3 Days |
10 Days |
Vendor disruption events |
|
Emergency Procurement |
8.8 |
Operational Continuity |
3 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
4 Hr |
1 Day |
Crisis or urgent requirement |
|
Procurement System & Data Management |
8.9 |
Digital Operations / Data Access |
3 |
4 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
5 |
1 Day |
3 Days |
System failure/downtime |
Legend
- Impact Scale (1–5):
1 = Negligible
2 = Minor
3 = Moderate
4 = Significant
5 = Severe - RTO (Recovery Time Objective): The maximum acceptable downtime before recovery must occur to avoid a significant impact.
- MTPD (Maximum Tolerable Period of Disruption): The maximum time a process can be disrupted before causing unacceptable impact.
- Vulnerable Period: Timeframes during which disruptions have heightened risk due to business cycles or operational dependencies.
Summing Up ... for Part 3
The findings in this chapter provide a time-based perspective on the vulnerabilities and criticality of Bandtree’s operations.
The structured evaluation of each business function’s impact over time enables informed prioritisation of recovery efforts and resource planning during disruptions.
Key insights from this chapter—such as which functions must be restored within hours versus days—will inform the development of targeted recovery strategies in the next phase of the Business Continuity Management (BCM) process.
These insights also help ensure alignment with Bandtree’s Minimum Business Continuity Objectives (MBCOs) and support compliance with internal policies and external regulatory requirements.
Ultimately, understanding how impacts evolve strengthens Bandtree’s resilience posture and enhances its capacity to maintain service delivery, uphold stakeholder confidence, and recover effectively from any disruptive event.
.

BIA Questionnaires
CBF-8: Procurement & Supply Chain Management
 The effective functioning of CBF-8: Procurement & Supply Chain Management at Bandtree Brunei relies heavily on a suite of digital tools and applications that support procurement planning, vendor engagement, inventory tracking, contract governance, and risk mitigation.
The effective functioning of CBF-8: Procurement & Supply Chain Management at Bandtree Brunei relies heavily on a suite of digital tools and applications that support procurement planning, vendor engagement, inventory tracking, contract governance, and risk mitigation.
Purpose of Chapter
This chapter identifies the critical IT systems and applications that underpin each sub-process of the procurement function, outlining their Recovery Point Objectives (RPOs), System Recovery Time Objectives (System RTOs), and dependencies on specialized equipment or resources.
Given the time-sensitive and high-value nature of procurement activities—particularly during emergencies or project deadlines—it is imperative to ensure high availability, swift recovery, and data integrity of supporting systems.
These applications enable seamless coordination between departments, vendors, and external regulatory stakeholders, ensuring operational continuity and compliance with organisational and national procurement standards.
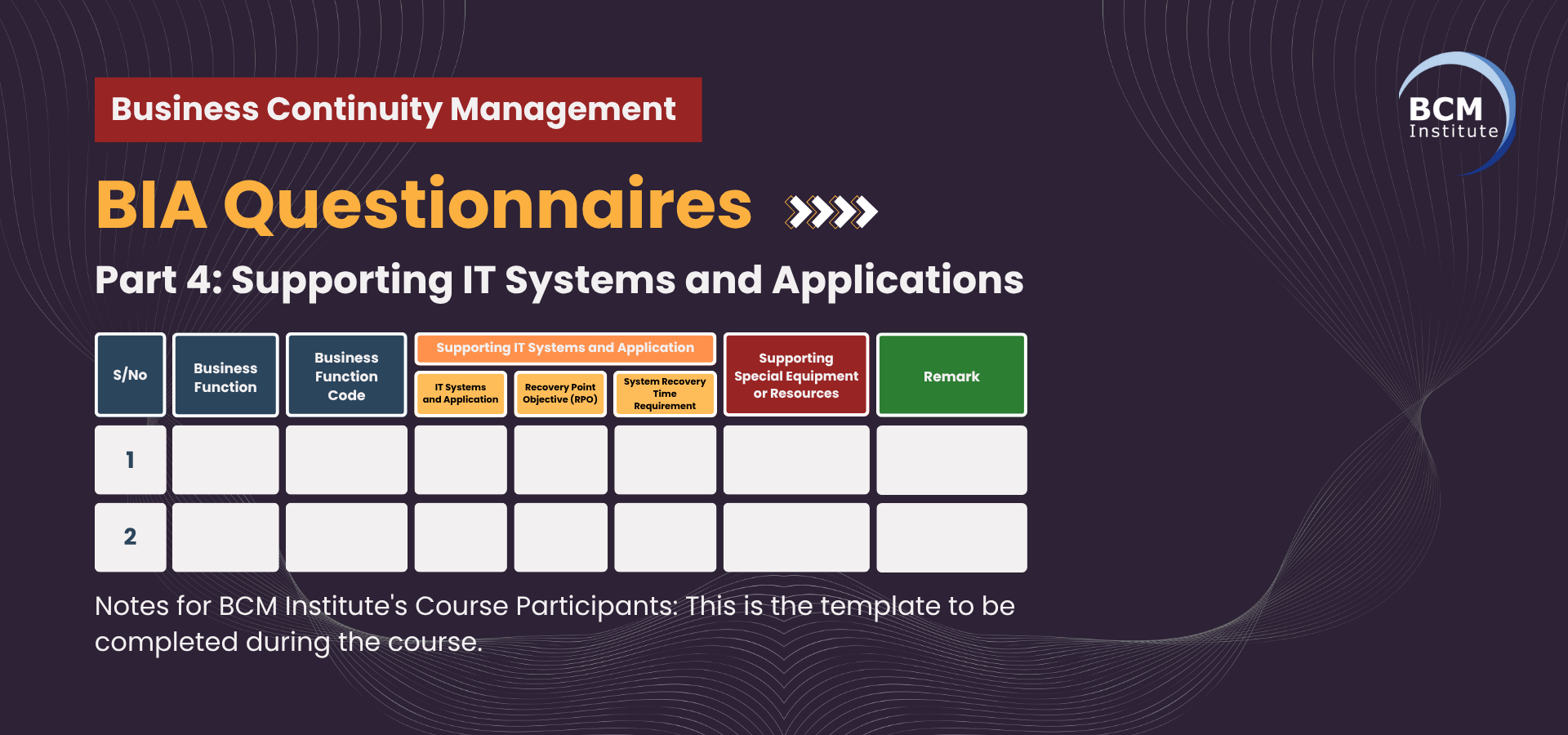
Below is the requested table for CBF-8: Procurement & Supply Chain Management of Bandtree Brunei, detailing the IT systems and applications, Recovery Point Objective (RPO), System Recovery Time Objective (RTO), supporting special equipment and resources, and additional remarks for each sub-process.
Table 4: [BIA] [P4] Supporting IT Systems and Applications for CBF-8: Procurement & Supply Chain Management
|
Sub-CBF |
Sub-CBF Code |
IT Systems and Applications |
RPO |
System RTO |
Supporting Special Equipment or Resources |
Remarks |
|
Vendor Selection & Prequalification |
8.1 |
Vendor Evaluation Portal, Email |
24 hrs |
48 hrs |
Secure internet access, evaluation templates |
Requires updated vendor databases and scoring tools |
|
Contract Management |
8.2 |
Contract Lifecycle Management (CLM) |
12 hrs |
24 hrs |
Secure document repository, e-signature devices |
Legal templates and a renewal tracking system are critical |
|
Purchase Requisition & Approval |
8.3 |
ERP System (e.g., SAP/Oracle) |
4 hrs |
8 hrs |
User access terminals, approval tokens |
Delay affects the procurement cycle and inventory ordering |
|
Supplier Relationship Management |
8.4 |
Supplier Portal, CRM |
24 hrs |
48 hrs |
Communication devices, contact database |
Long-term service quality and response tracking depend on system access |
|
Inventory & Logistics Coordination |
8.5 |
Inventory Management System (IMS) |
4 hrs |
12 hrs |
Barcode scanners, warehouse terminals |
Physical asset visibility and dispatch coordination depend on real-time data |
|
Compliance & Procurement Governance |
8.6 |
Compliance Monitoring Tools |
12 hrs |
24 hrs |
Audit support tools, policy reference systems |
Necessary to meet audit and regulatory deadlines |
|
Risk Management in Supply Chain |
8.7 |
Risk Monitoring Dashboard, BI Tools |
24 hrs |
48 hrs |
Risk tracking sheets, analytics infrastructure |
Enables proactive vendor disruption mitigation |
|
Emergency Procurement |
8.8 |
ERP Emergency Module, Mobile Access |
2 hrs |
4 hrs |
Mobile procurement devices, rapid approval access |
Requires rapid activation for urgent needs (e.g. facility outages) |
|
Procurement System & Data Management |
8.9 |
Central Procurement System (e.g., SAP SRM) |
1 hr |
4 hrs |
Cloud backup, DR-enabled servers |
The core system for all procurement activities must be regularly backed up |
Legend
- RPO (Recovery Point Objective): Maximum acceptable data loss measured in time.
- System RTO (Recovery Time Objective): Maximum acceptable downtime before system functionality must be restored.
- Special Equipment/Resources: Tools, devices, or infrastructure necessary to support the system's operational continuity.
Summing Up ... for Part 4
The analysis of supporting IT systems and applications confirms that uninterrupted access to digital tools is critical to maintaining the integrity and efficiency of Bandtree’s procurement and supply chain operations.
Downtime or data loss in these systems could cause severe disruptions in inventory management, vendor coordination, compliance reporting, and emergency procurement response.
To mitigate these risks, Bandtree must maintain robust IT disaster recovery capabilities, including system redundancy, cloud backups, and clearly defined Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) for each core system.
This chapter serves as a key input for IT continuity planning, ensuring that procurement sub-CBFs are prioritised appropriately in the event of a disruption and can be recovered within tolerable timeframes to meet business and stakeholder expectations.
More Information About Business Continuity Management Courses
To learn more about the course and schedule, click the buttons below for the BCM-300 Business Continuity Management Implementer [BCM-3] and the BCM-5000 Business Continuity Management Expert Implementer [BCM-5].


















![Register [BL-B-3]*](https://no-cache.hubspot.com/cta/default/3893111/ac6cf073-4cdd-4541-91ed-889f731d5076.png)



![FAQ [BL-B-3]](https://no-cache.hubspot.com/cta/default/3893111/b3824ba1-7aa1-4eb6-bef8-94f57121c5ae.png)
![Email to Sales Team [BCM Institute]](https://no-cache.hubspot.com/cta/default/3893111/3c53daeb-2836-4843-b0e0-645baee2ab9e.png)





