BIA Questionnaires
CBF 6: Information Systems & Records Management
 In today’s digitally-driven business environment, Information Systems and Records Management form the backbone of organisational efficiency, compliance, and decision-making.
In today’s digitally-driven business environment, Information Systems and Records Management form the backbone of organisational efficiency, compliance, and decision-making.
The CBF-6: Information Systems & Records Management encompasses a wide range of essential activities, including ICT infrastructure management, cybersecurity, data backup, recovery, and physical records handling. Understanding the impact of disruptions to these functions over time is vital to developing effective continuity plans and minimising operational risks.
Purpose of Chapter
This chapter explores the temporal dimension of impact—how interruptions to each sub-process within CBF-6 evolve from the initial hours to weeks following an incident.
By evaluating the criticality and degradation of these functions over specific time intervals, the organisation can prioritise recovery strategies, allocate resources effectively, and safeguard its technological and informational assets.
Through a detailed impact-over-time assessment, we aim to provide a clear framework for maintaining resilience in Information Systems & Records Management amid potential disruptions.

 The analysis considers the Recovery Time Objective (RTO), Maximum Tolerable Period of Disruption (MTPD), and periods of heightened vulnerability for each sub-process.
The analysis considers the Recovery Time Objective (RTO), Maximum Tolerable Period of Disruption (MTPD), and periods of heightened vulnerability for each sub-process.
This structured approach enables Bandtree to prioritise response efforts, allocate resources effectively, and enhance overall resilience in the face of unexpected disruptions.
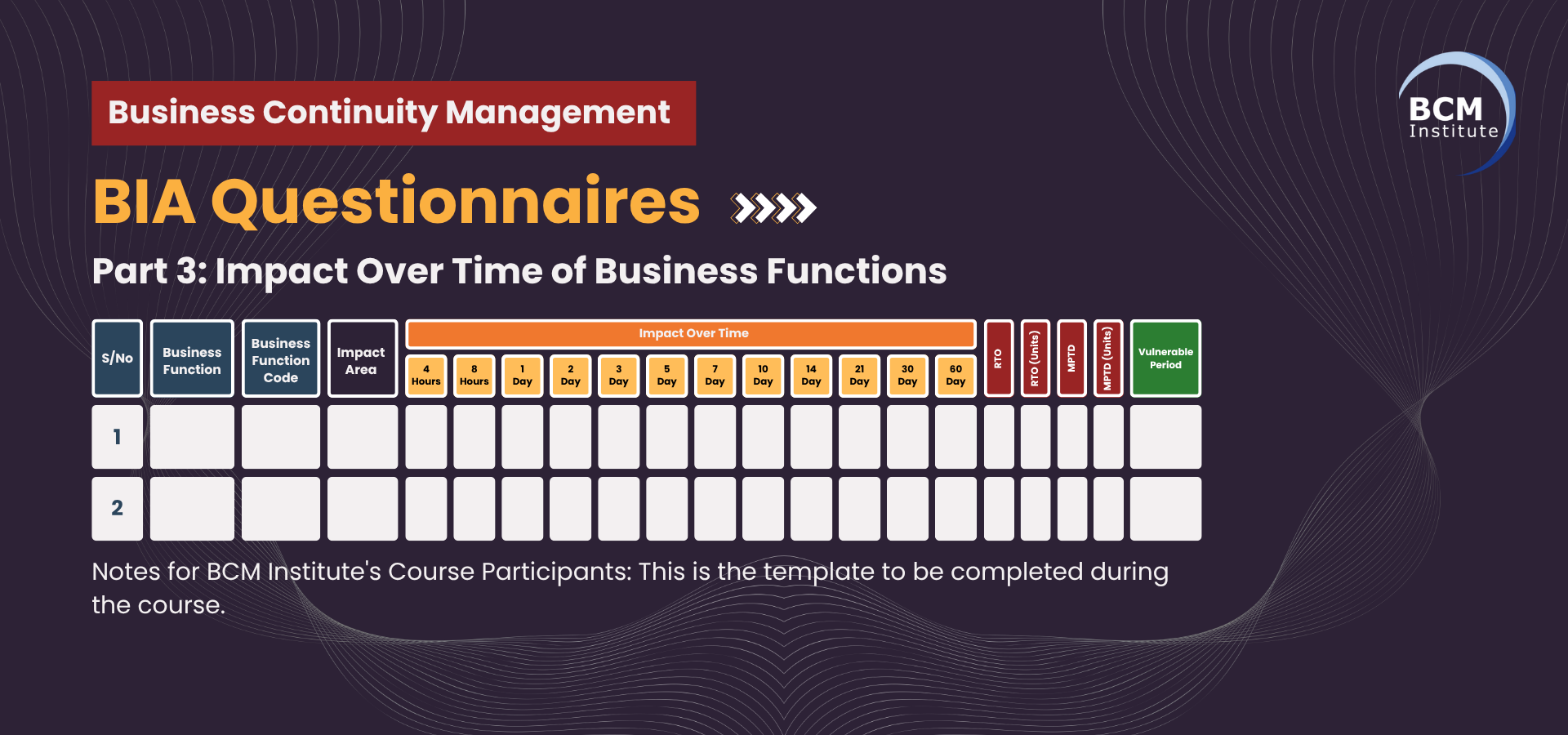
This table outlines the CBF-6: Information Systems & Records Management and its sub-processes (Sub-CBFs) for Bandtree, following the impact over time methodology from BCM Institute's guidance Notes and using a 1–5 severity scale.
Table 3-1: [BIA] [P3] Impact Over Time of Business Functions (Sub-CBF) for CBF-6 Information Systems & Records Management
|
|
|
|
Impact Over Time | |||||||||||
|
Sub-CBF |
Sub-CBF Code |
Highest-Impact Area |
4 Hour |
8 Hour |
1 Day |
2 Day |
3 Day |
5 Day |
7 Day |
10 Day |
14 Day |
21 Day |
30 Day |
60 Day |
|
ICT Infrastructure Management |
6.1 |
Network & System Availability |
5 |
5 |
5 |
4 |
3 |
2 |
1 |
1 |
1 |
1 |
1 |
1 |
|
Property Systems Application Support |
6.2 |
Application Uptime & Access |
5 |
5 |
4 |
3 |
3 |
2 |
1 |
1 |
1 |
1 |
1 |
1 |
|
Records Retention & Archiving |
6.3 |
Data Integrity & Compliance |
5 | 4 |
3 |
3 |
3 |
2 |
2 |
1 |
1 |
1 |
1 |
1 |
|
Data Backup & Recovery |
6.4 |
Data Restoration Capability |
5 |
5 |
5 |
4 |
4 |
3 |
3 |
2 |
2 |
2 |
1 |
1 |
|
Cybersecurity & Access Control |
6.5 |
Security Breach Prevention |
5 | 5 | 5 | 4 | 4 | 3 | 3 | 2 | 2 | 2 | 1 | 1 |
|
System Development & Enhancement |
6.6 |
System Stability & Features |
3 | 3 | 3 | 3 | 2 | 2 | 2 | 2 | 1 | 1 | 1 | 1 |
|
ICT Vendor Management |
6.7 |
Service Continuity & SLA |
3 | 3 | 2 | 2 | 2 | 2 | 2 | 1 | 1 | 1 | 1 | 1 |
|
User Training & Support |
6.8 |
User Efficiency & Issue Resolution |
3 | 3 | 3 | 3 | 2 | 2 | 2 | 1 | 1 | 1 | 1 | 1 |
|
Compliance & IT Governance |
6.9 |
Regulatory & Policy Compliance |
4 | 4 | 3 | 3 | 3 | 2 | 2 | 2 | 2 | 2 | 1 | 1 |
|
Physical Records Handling |
6.10 |
Physical Security & Access |
3 | 3 | 3 | 3 | 2 | 2 | 2 | 1 | 1 | 1 | 1 | 1 |
Table 3-2: [BIA] [P3] Impact Over Time of Business Functions (Sub-CBF) for CBF-6 Information Systems & Records Management
|
|
|
|
|
|
|
Sub-CBF |
Sub-CBF Code |
RTO |
MTPD |
Vulnerable Period |
|
ICT Infrastructure Management |
6.1 |
8 hours |
3 days |
The initial 24 hours are critical |
|
Property Systems Application Support |
6.2 |
12 hours |
5 days |
24-48 hours critical |
|
Records Retention & Archiving |
6.3 |
24 hours |
7 days |
2 days critical |
|
Data Backup & Recovery |
6.4 |
6 hours |
3 days |
The first 12 hours are critical |
|
Cybersecurity & Access Control |
6.5 |
4 hours |
2 days |
Immediate critical |
|
System Development & Enhancement |
6.6 |
1 day |
10 days |
Less critical early |
|
ICT Vendor Management |
6.7 |
2 days |
14 days |
Moderate critical |
|
User Training & Support |
6.8 |
1 day |
7 days |
Moderate critical |
|
Compliance & IT Governance |
6.9 |
12 hours |
7 days |
Early 24-hour critical |
|
Physical Records Handling |
6.10 |
1 day |
10 days |
Moderate critical |
Legend – Impact Scores
- 1 = Negligible Impact (Very Low)
- 2 = Minor Impact (Low)
- 3 = Moderate Impact (Medium)
- 4 = Major Impact (High)
- 5 = Critical/Catastrophic Impact (Very High)
Key Notes
- RTO (Recovery Time Objective): Indicates the acceptable downtime before severe impact begins.
- MTPD (Maximum Tolerable Period of Disruption): Maximum allowable time the sub-function can be disrupted before irrecoverable consequences occur.
- Vulnerable Period: Timeframes in which disruption has amplified effects (e.g., audits, contract renewals, public reporting).
Summing Up... Part 3
The assessment of impact over time for CBF-6 Information Systems & Records Management highlights the varying degrees of urgency and tolerance for disruption across its sub-functions.
While certain areas, such as cybersecurity and data backup, require immediate restoration to prevent severe operational and reputational damage, other functions, like system development and vendor management, allow for slightly extended recovery periods.
This nuanced understanding enables Bandtree to tailor its business continuity and disaster recovery efforts specifically to the time-sensitive needs of each sub-process.
Prioritising rapid recovery for high-impact areas and maintaining flexible response plans for less critical functions will strengthen the organisation’s overall resilience.
Ultimately, this temporal impact analysis forms a crucial pillar in safeguarding Bandtree’s information infrastructure and ensuring uninterrupted support for its corporate property management operations.
BIA Questionnaires
CBF 6: Information Systems & Records Management
In today’s digital-driven business environment, the efficiency and resilience of supporting IT systems and applications are fundamental to the seamless operation of Information Systems and Records Management.
systems and applications are fundamental to the seamless operation of Information Systems and Records Management.
Purpose of Chapter
This chapter explores the critical technology platforms, software applications, and infrastructure that underpin Bandtree’s corporate property management functions.
Emphasis is placed on how these systems facilitate data integrity, secure records management, user accessibility, and business continuity.
By understanding the role and interdependencies of these IT components, stakeholders can better appreciate the foundation that supports Bandtree’s operational excellence and compliance in the dynamic real estate sector.
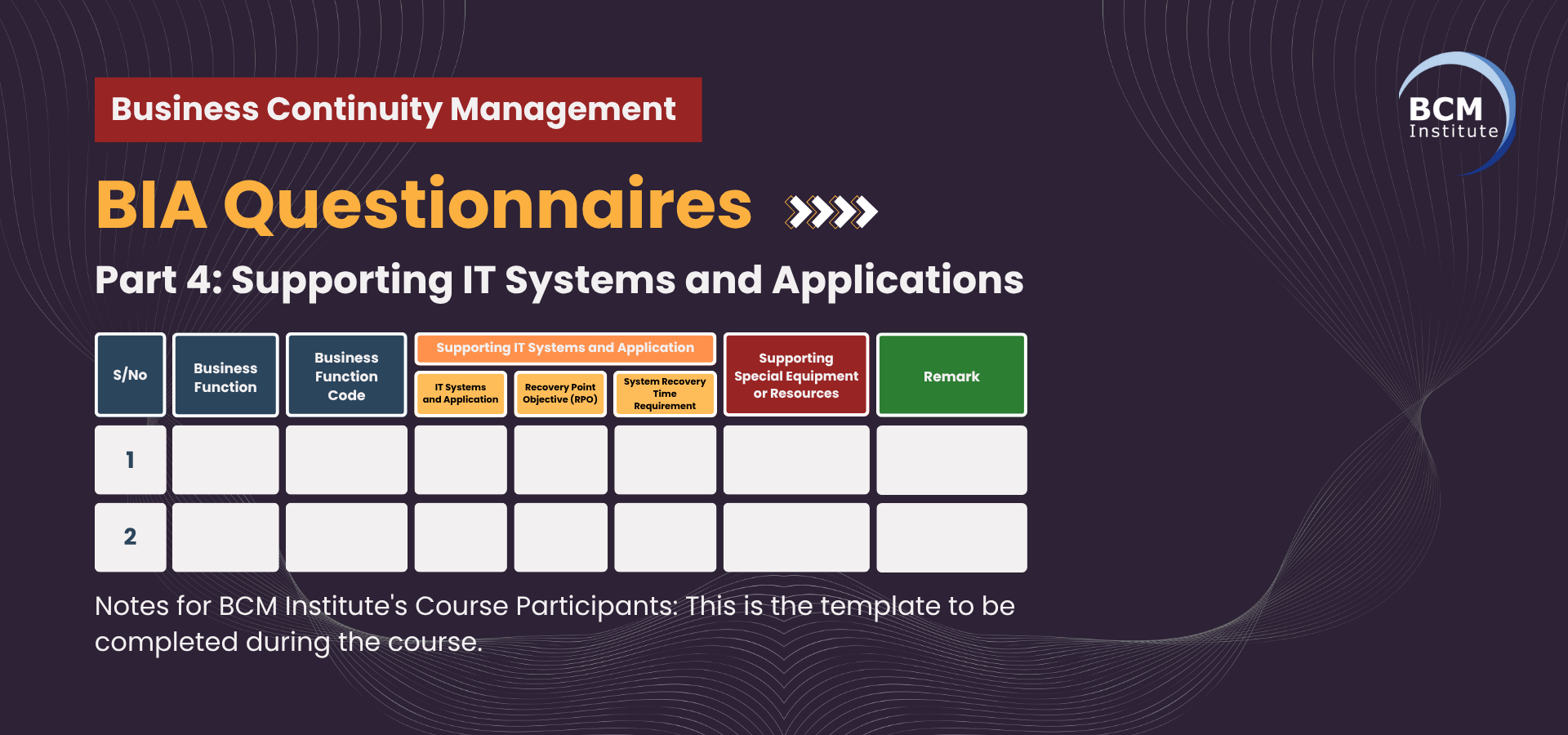
Here is a detailed table for CBF-6: Information Systems & Records Management and its Sub-CBFs, designed for Bandtree with the specified headers:
Table 4-1: [BIA] [P4] Supporting IT Systems and Applications for CBF-6 Information Systems & Records Management
|
|
|
Supporting IT Systems | ||
|
Sub-CBF |
Sub-CBF Code |
IT Systems and Applications |
RPO |
System RTO |
|
ICT Infrastructure Management |
6.1 |
Network management tools, server OS |
< 4 hours |
4 hours |
|
Property Systems Application Support |
6.2 |
Property management software |
< 8 hours |
8 hours |
|
Records Retention & Archiving |
6.3 |
Document management systems |
< 24 hours |
24 hours |
|
Data Backup & Recovery |
6.4 |
Backup software and cloud storage |
< 1 hour |
2 hours |
|
Cybersecurity & Access Control |
6.5 |
Security monitoring tools, IAM systems |
Immediate |
Immediate |
|
System Development & Enhancement |
6.6 |
Development platforms, version control systems |
N/A |
N/A |
|
ICT Vendor Management |
6.7 |
Vendor management platforms |
N/A |
N/A |
|
User Training & Support |
6.8 |
Helpdesk software, e-learning platforms |
N/A |
N/A |
|
Compliance & IT Governance |
6.9 |
Compliance tracking and audit software |
N/A |
N/A |
|
Physical Records Handling |
6.10 |
Physical storage management systems |
N/A |
N/A |
Table 4-2: [BIA] [P4] Supporting IT Systems and Applications for CBF-6 Information Systems & Records Management
|
|
|
|
|
|
Sub-CBF |
Sub-CBF Code |
Supporting Special Equipment or Resources |
Remarks |
|
ICT Infrastructure Management |
6.1 |
Network switches, firewalls, and servers |
Critical to maintain connectivity and system availability |
|
Property Systems Application Support |
6.2 |
Application servers, database servers |
Supports core property management business operations |
|
Records Retention & Archiving |
6.3 |
Secure digital archives and physical storage facilities |
Ensures regulatory compliance and records preservation |
|
Data Backup & Recovery |
6.4 |
Backup servers, cloud backup platforms |
Essential for data protection and restoration |
|
Cybersecurity & Access Control |
6.5 |
Firewalls, intrusion detection systems, and multi-factor authentication devices |
Protects against cyber threats and unauthorised access |
|
System Development & Enhancement |
6.6 |
Dev environments, testing servers |
Ongoing improvements to systems to meet business needs |
|
ICT Vendor Management |
6.7 |
Communication tools, contract databases |
Coordinates with external IT service providers |
|
User Training & Support |
6.8 |
Training rooms, support tools |
Ensures users can effectively use ICT systems |
|
Compliance & IT Governance |
6.9 |
Reporting tools, documentation systems |
Maintains adherence to IT policies and regulations |
|
Physical Records Handling |
6.10 |
Secure filing cabinets, access controls |
Manages physical document security and access |
Summing Up ... for Part 4
The supporting IT systems and applications detailed in this chapter form the backbone of Bandtree’s Information Systems and Records Management capabilities.
Their robustness, security, and adaptability not only ensure ongoing operational stability but also empower the organisation to respond swiftly to emerging challenges and technological advancements.
Maintaining and enhancing these systems remains a strategic priority to uphold data integrity, compliance requirements, and efficient service delivery.
As Bandtree continues to evolve, the integration and optimisation of its IT landscape will be essential in sustaining its role as a trusted government-linked company in Brunei Darussalam.
More Information About Business Continuity Management Courses
To learn more about the course and schedule, click the buttons below for the BCM-300 Business Continuity Management Implementer [BCM-3] and the BCM-5000 Business Continuity Management Expert Implementer [BCM-5].



















![Register [BL-B-3]*](https://no-cache.hubspot.com/cta/default/3893111/ac6cf073-4cdd-4541-91ed-889f731d5076.png)



![FAQ [BL-B-3]](https://no-cache.hubspot.com/cta/default/3893111/b3824ba1-7aa1-4eb6-bef8-94f57121c5ae.png)
![Email to Sales Team [BCM Institute]](https://no-cache.hubspot.com/cta/default/3893111/3c53daeb-2836-4843-b0e0-645baee2ab9e.png)





